Solution
The Microsoft Windows cumulative updates will have no impact on OPC UA Connection and the changes will only impact OPC DA.Please follow below steps to disable the new security.
- Kepware products can be set to use the newly required (by Microsoft) DCOM security with the Windows DCOM configuration utility (DCOMCNFG.EXE). No patch is required
- The DCOM Authentication Level will need to be set to Packet Level Integrity for both the Client and the Server.
- For Server applications this change will need to be made at the Application level:
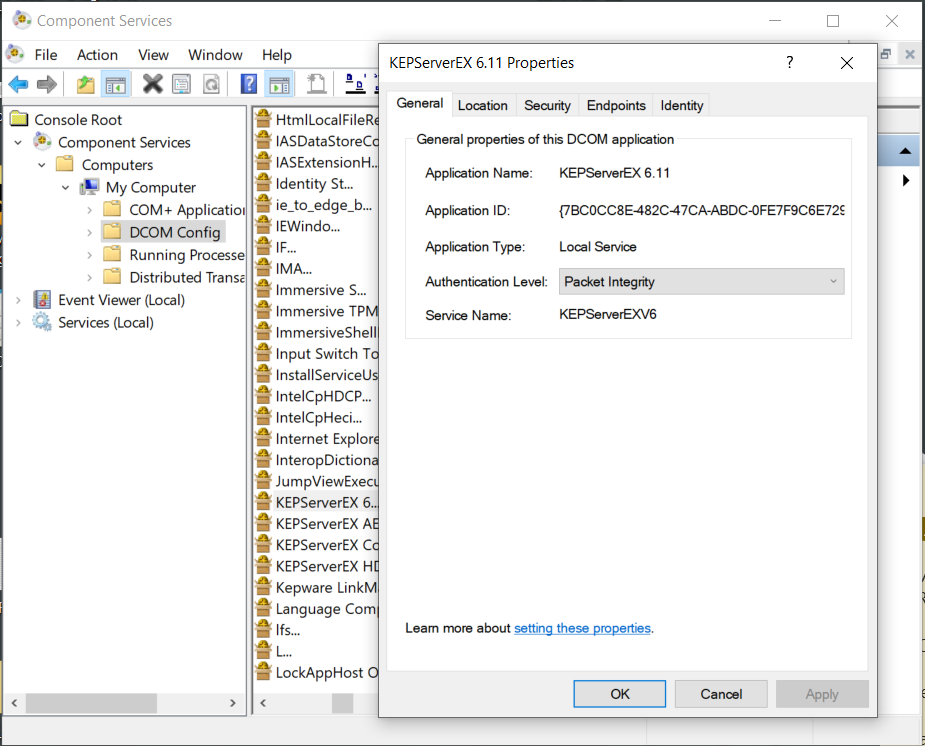
3. For
Client applications this change will need to be made at the
My Computer level:
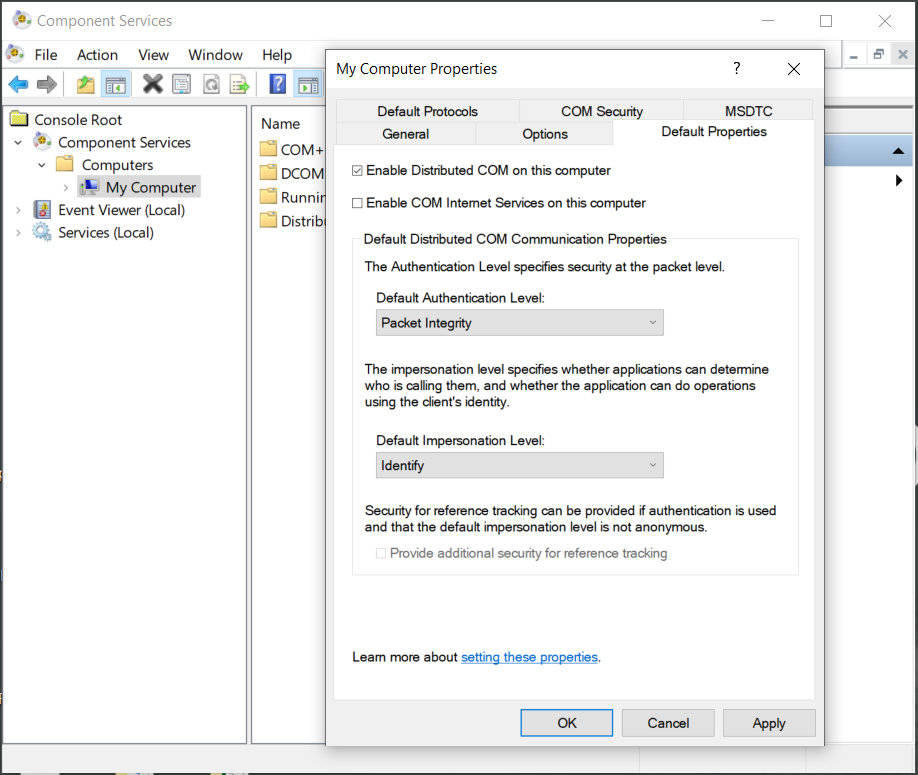
- Note: KEPServerEX may be the Client, Server or both
- In addition to DCOM configuration, the following product settings must be enabled:
1. KEPServerEX; ThingWorx Kepware Server; OPC Aggregator: Settings>Runtime Options>
Use DCOM configuration settings
2. OPC Quick Client:Tools>Options>
Use DCOM for remote security
3. LinkMaster: Tools>Options>Runtime Options>
Use DCOM configuration utility settings
Other resolution options:
- Move OPC-DA clients and servers to the same workstation
- Migrate the system to replace Classic OPC-DA with OPC UA